FIDO® Suite
FIDO® certified SDKs for mobile biometric authentication
Aware’s FIDO® Suite is a family of SDKs for mobile biometric authentication that are certified conformant with the specifications of the FIDO Alliance and interoperable with other FIDO-certified products. Aware’s Face and Face+Voice Authenticators are UAF v1.1 Level 1 FIDO® Certified.
How it works – Registration
FIDO authentication employs a challenge/response mechanism using digital signatures. A user must first access a specific app or website and complete a registration process before using FIDO. The user submits their biometrics and PIN during this registration.For every successful biometric/PIN match during registration, a public key pair is created. The private key is retained on the client in a cryptographic keystore, and the public key is sent to the server, where it is saved in a keystore under the user’s ID.
How it works – Login
Upon a login attempt, FIDO Server creates a random challenge and sends it to the FIDO Client. The biometrics and PIN are matched locally by the FIDO Authenticator against the biometrics enrolled for that user; they are never transmitted to the server. The user is prompted again to enter his biometrics/PIN. If the match attempt is successful, it unlocks the private key from the FIDO Client keystore. The FIDO Client signs the challenge using the user’s private key and sends it to the FIDO Server. The server verifies the signature using the public key received during registration, and the user is permitted to login.
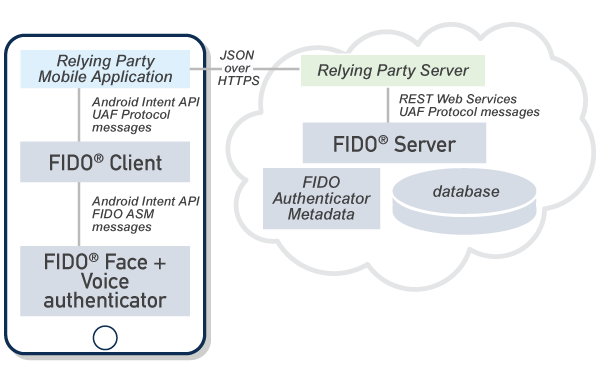
FIDO Authenticators
Aware’s FIDO Authenticators allow a user to login to a mobile application of a relying party (such as a banking app) using their face and (optionally) voice for authentication. The captured biometrics never leave the security boundaries of the authenticator application. Aware’s Face and Face+Voice Authenticators are UAF v1.1 Level 1 FIDO® Certified.
Each time the user logs in to the mobile application using FIDO, their biometrics are verified against the template stored on the device. Once verified, the private key is unlocked from the device and a signature is created on a challenge, which is send to the server. The server verifies the challenge using the stored public key, thus enabling the login process to complete.The interfaces exposed by Aware’s FIDO Authenticators are standardized by the FIDO ASM (Authenticator-Specific Module) API. It uses JSON messages to communicate with the FIDO UAF Client residing on the same device.
FIDO® Face Authenticator
![]()
Aware’ FIDO Face Authenticator uses facial recognition for biometric authentication, with a user interface that enables a user to capture his/her face and robust active and passive liveness detection techniques to prevent spoofing. The captured face and voice data is stored in a template form, and is used for subsequent login to FIDO-enabled servers.
FIDO® Face+Voice Authenticator
Aware’s FIDO Face+Voice Authenticator uses both face and voice recognition and liveness detection for biometric authentication. It captures face and voice simultaneously during authentication, applying active and passive face and voice-based liveness detection methods to prevent spoofing attacks.
Features & Functionality
FIDO Client
![]()
FIDO® Client is the intermediary application that helps to bind FIDO authenticators with the relying party mobile application. A FIDO client can look up all FIDO authenticators on the device, and communicate via JSON messages standardized by the FIDO ASM API. Similarly, a relying party mobile application can look up a FIDO client and communicate with FIDO Client. The messages between a relying party application and FIDO Client are standardized via FIDO UAF Protocol Specification and FIDO UAF Application API specification.FIDO Client can create an UAF Protocol payload, embed it as part of a larger message, and transmit it via the Android intent mechanism to the mobile application layer. The application could embed this message as part of its payload to the relying party server, which then communicates with a FIDO server.FIDO Client serves as the glue that can link any relying party mobile application that requires the FIDO functionality with the different FIDO authenticators on the device, possibly provided by different vendors.
Features & Functionality
FIDO Server
![]()
FIDO® Server enables a relying party server to offer FIDO-based login from their mobile applications. FIDO® Server encapsulates the FIDO features required at the server, such as maintenance of the FIDO login policies, management of the public keys, and verification of the signatures created on the mobile device. It exposes REST-style web services that can be consumed by a relying party server to enable FIDO functionality.The messages consumed or generated by the FIDO Server are also governed by the FIDO UAF Protocol Specification. A relying party server and mobile applications act as carriers of the UAF protocol messages.
Features & Functionality
About FIDO
FIDO specifications aim to define frameworks for authentication online from PCs and mobile devices. There are two sets of FIDO specifications: UAF (Universal Authentication Framework) for passwordless authentication, and U2F (Universal 2nd Factor) for second-factor authentication. Aware’s FIDO® Suite products are certified compliant with the FIDO specifications for UAF. They include three categories of products: FIDO Server, FIDO Client, and FIDO Authenticators.
UAF enables a user to login to a website using biometrics or other means instead of a password. FIDO specifications ensure that private identity information including biometrics is always captured, verified and retained on the user’s device and never sent remotely up to a server. FIDO also offers plugability, by modularizing the architectural into various components, each with standardized interfaces that facilitate interoperability.
FIDO® is a trademark (registered in numerous countries) of FIDO Alliance, Inc.